Security
The IT department supports campus staff, faculty, administrators, and students in protecting the confidentiality, integrity, and availability of sensitive information, critical systems, and other important information assets. Our activities include education, vulnerability testing, software security evaluation, and periodic audits.
To report an information security incident, compromise, or data breach, please see .
To learn more about information security policies and standards that apply to Sonoma State University, see .
Security Help Articles
Level I (Confidential)
Level I data is the most sensitive data we handle, which can cause potentially severe damage to the CSU, its students, its employees, or its customers if breached.
Examples of Level I data*:
- Username or email address, in combination with a password or security question/answer that would permit access to an online account
- Birth date combined with the last four digits of SSN and name
- Credit card numbers with cardholder name
- Tax ID with name
- Driver’s license number, state identification card, and other forms of national/ international identification (such as passports, visas, etc.) in combination with name
- Social Security number and name
- PINs (Personal Identification Numbers)
- Medical records related to an individual (also including information about disabilities, limitations, injuries, and health insurance information)
* This list is incomplete and describes the most common examples. See below for additional resources.
How to protect Level I data:
- Never send through email
- Never store in Google Drive
- Never store on any other unapproved cloud service such as Dropbox
- Never store on the SSU-beta file server (check with the IT Help Desk for more info)
- Never store on an unencrypted flash drive or external drive
- Must be encrypted when transported over the network, and should be encrypted whenever possible during storage
- Must only be stored or accessed using University owned and managed equipment
- Must be accessed using multifactor authentication
- May only be accessed by users with a legitimate business use for the data
Level I data may be:
- Stored on drives with full disk encryption, including flash drives
- Stored in OnBase
- Transmitted using MoveIt Transfer
- Stored on the SSU-Alpha fileserver (check with the IT Help Desk for more info)
Level II (Internal User)
Level II data must be protected due to proprietary, ethical, contractual, or privacy considerations.
Examples of Level II data*:
- Identity Validation Keys (name with)
- Birth date (full: mm-dd-yy)
- Birth date (partial: mm-dd only)
- Photo (taken for identification purposes)
- Student Information-Educational Records not defined as “directory” information, typically:
- Grades
- Courses taken
- Schedule
- Test Scores
- Advising records
- Educational services received
- Disciplinary actions
- Student photo
- Library circulation information
* This list is incomplete and describes the most common examples. See below for additional resources.
Level II data may be:
- Only accessed by users with a legitimate business use for the data
- Sent through email
- Stored in Google Drive
- Stored on the SSU-beta or SSU-alpha file servers
- Stored on an unencrypted flash drive or external drive
- Stored on drives with full disk encryption, including flash drives
- Stored in OnBase
- Transmitted using MoveIt Transfer
Level III (General)
Level III (General) data may be shared publicly, if the University chooses to do so.
Resources for additional information regarding ALL Level data:
- ISO Domain 8: Asset Management Standard
- Information Asset Management from the SSU Information Security Management Program
- ISO Domain 12: Access Control Standard
- Access Control Standard from the SSU Information Security Management Program
- Configuration Management Standard from the SSU Information Security Management Program
Overview
In an effort to protect and maintain data security on our campus, SSU is required to track systems, workstations, and users who store and/or have access to high risk information. Per the High Risk/Critical Workstation Standard, a High Risk Workstation is any workstation that is used for elevated access to critical systems or stores or accesses level 1 information in such quantities as to require notification of a government entity (i.e. over 500 records under HIPAA or CA 1798.29), or information classified as protected level 1 due to severe risk.
Level 1 data is defined as confidential information that include (but are not limited to):
- Passwords or credentials that grant access to level 1 and level 2 data
- PINs (Personal Identification Numbers)
- Birth date combined with last four digits of SSN and name
- Credit card numbers with cardholder name
- Tax ID with name
- Driver’s license number, state identification card, and other forms of national/ international identification (such as passports, visas, etc.) in combination with name
- Social Security number and name
- Health insurance information
Additional information regarding data definitions can be found on our website.
Critical systems are systems that access level 1 date and/or are necessary to conduct University business.
Impact to Users
Users identified as high risk with access to level 1 data and/or critical systems can only access sensitive data systems through high risk workstations. When a high risk user logs into a machine, that machine becomes high risk, receives the high risk configurations via group policy, and is added to an inventory of high risk workstations. High risk users who try logging into non-high risk configured workstations will be met with the following prompt:
“WARNING! User Account __________ has been identified as a High Risk User Account. However this Device ____________ is Not setup for High Risk Access. If you continue this Device will be automatically secured for High Risk Access and IT will be notified. Non High Risk User Accounts will lose access to this device. Do you want to Continue Logging into this compers?
Do not log into a non-high risk workstation.
User Login Behavior by Workstation Type
| Type of Computer | High Risk User | Non-High Risk User |
| Department Computers | It displays a message and moves it to the high risk OU. | No change. |
| Lab Computers | They are denied login. | No change. |
| Library Computers | They are denied login. | No change. |
| IT Loaner Computers | It displays a message and moves it to the high risk OU. | No change. |
| High Risk Computers | No change. | They are denied login. |
| High Risk Department (Counseling, SHC, IT, PD, etc.) | No change. | They are denied login. |
Encrypted Flash Drives
High risk users can no longer use unencrypted USB flash drives for external storage. High risk workstation configurations allow for reading unencrypted USB flash drives but not saving new files to them. Users can encrypt unencrypted drives using Bitlocker Drive Encryption. The following prompt will appear when plugging an unencrypted USB flash drive to a high risk workstation.
Network Protections
High risk users with desktops are connected to a section of the campus network that is specifically configured for high risk access. Once a person is identified as high risk, the IT Department will submit a ticket on the user's behalf to move their machine(s) to the appropriate secured network.
High risk users with laptops are protected by an always-on VPN connection, which ensures high risk workstations are isolated and can only connect to SSU’s protected VPN network that provides the same level of protection as the high risk network. If you have a laptop, connect to Global Protect to enable always-on VPN. Connecting to off-campus networks, such as a coffee shop or hotel wifi, should work via a captive portal.
Information for Administrators of High Risk/Critical Systems
If you have been identified as an administrator of a high risk/critical system, you are responsible for identifying users who are granted access to level 1 data. In order to track the appropriate access, those users with access must be added to or removed from the group created for that system.
Log into the Application Access Manager (AAM) tool using your SSU username and password.
- To add members, search for people to add by entering an ID (LDAP UID, Emplid, Regid, etc.) or Last Name in the Search Term field below, then click the "Search" button.
- To remove members, select the member or members you want to remove by clicking on them in the select box below, then click the "Remove Selected Members" button to remove them.
- To make changes to the administrator, such as adding a new administrator or removing an existing administrator, please contact the IT Help Desk.
- To add a new critical system or remove a critical system that is no longer in use, please contact the IT Help Desk.
General Information
Please note that users should refrain from accessing level 1 data and/or critical systems until they have received confirmation that workstation configuration and network changes have been made to your device(s). It is important that high risk users back-up their data to avoid accidental data loss. Do not store level 1 data on Google Drive. Options for storing and transmitting level 1 data can be found on our Data Security Quick Guide.
Here are some general guidelines to follow that will reduce your risk when using computers and the Internet:
- Be alert for phishing and other email related scams. See the Phishing FAQ for more details
- Use a different password for every account. If you reuse the same password then an attacker who compromises one service you use, or an unscrupulous administrator of that service, can use that password to break into your other accounts.
- Ensure your operating system and all installed software is still supported by the developer and that security updates are being released.
- Apply updates to your operating system and all installed software regularly. Consider enabling automatic software updates.
- Install and maintain anti-virus software. The SSU IT Malware: Viruses, Trojans, and Spyware page has instructions as well as some recommendations on anti-virus software.
- Do not leave your computer, phone, tablet, or storage devices unattended in a public setting.
- Use full disk encryption on devices containing sensitive information.
- Configure screen locking features to protect your computer when you are not using it.
If there is an emergency, or if someone is in danger, call 911 right away.
Persons who suspect a security incident should contact the SSU IT Help Desk in one of the following ways:
- Send email to [email protected]; or
- Call 707-664-HELP (contact by email if there is no answer); or
- Visit the SSU IT Help Desk in Salazar Hall 1000.
If the IT Help Desk is closed and an Information Security incident is in the process of causing serious harm to the University or to individuals in the University community, telephone the University Police at 707-664-4444.
Please inform the IT Help Desk of the nature of data stored and accessed on any system suspected of being compromised to the extent that this can be done without using or accessing the system itself.
State, in particular if CSU-protected level 1 or 2 data violations are suspected, such as Social Security Numbers, medical information, grades, or other CSU-protected level 1 or 2 data as defined in the CSU Data Classification Standard.
This table links to specific sections of CSU and SSU security policies and standards.
Approved by President Ruben Arminaña and the Extended Cabinet on April 24, 2014.
Updates approved by Nate Johnson on May 20, 2015.
Updates approved by Douglass Berman on January 10, 2018.
Updates approved by the SSU Information Technology Advisory Committee on January 7, 2019.
Updates approved by the SSU Information Technology Advisory Committee on May 11th, 2020.
Updates approved by the SSU Information Technology Advisory Committee on March 7th, 2022.
1 Introduction
This Information Security Program describes how Sonoma State University will fulfill its obligations to protect those information assets for which Sonoma State University or its auxiliaries or other affiliated organizations hold ownership or responsibility.
2 Background
The CSU User Roles and Responsibilities Policy states that it is the collective responsibility of all users to ensure:
- Confidentiality of information that the CSU must protect from unauthorized access;
- Integrity and availability of information stored on or processed by CSU information systems;
- Compliance with applicable laws, regulations, and CSU/campus policies governing information security and privacy protection.
3 Program Goals
The goals of the Sonoma State University Information Security Program are to:
- Identify and manage information security risks and liabilities;
- Ensure compliance with all applicable laws, regulations, contracts, and California and CSU policies;
- Communicate responsibilities and minimum requirements.
4 Scope
The Sonoma State University Information Security Program applies to:
- All people, organizations, systems, networks, processes, media, and data for which Sonoma State University or its auxiliaries or other affiliated organizations hold ownership or responsibility; and
- All people, organizations, systems, networks, processes, media, and data to whom are given access to or custody of Information Assets for which Sonoma State University or its auxiliaries or other affiliated organizations hold ownership or responsibility.
5 Annual Review
The Information Security Officer, in collaboration with the Information Security Steering Committee, will annually review this program and will recommend needed revisions to the CIO for final review by the President and Information Technology Advisory Group (ITAG).
6 Should and Must Definition
Throughout this document, the words “must” and “should” have been carefully used to describe requirements. While both terms denote a requirement that needs to be followed, the process for making exceptions differs.
Exceptions to a "should" requirement must be approved by an appropriate administrator and by all affected data owners. The Information Security Office must also be notified of the exception.
Exceptions to a "must" requirement must be approved by an appropriate administrator, by all affected data owners, and by the Information Security Office.
In either case, exceptions are only to be granted if either:
- The risk addressed by the requirement does not exist in a given context; or
- The risk addressed by the requirement is being addressed by other controls that would compensate for not fulfilling the requirement.
7 Roles and Responsibilities Standard
Implements ISO Domain 6: Organization of Information Security Policy and the CSU Roles and Responsibilities Policy.
7.1 Data Owner or Data Authority
The roles of Data Owner and Data Authority have the same responsibilities and the terms are used interchangeably in the SSU Information Security Management Program. A Data Owner or Data Authority is responsible for decisions related to data access, use, storage, and protection of a particular type or collection of data. The data owner or data authority is an individual, not a group, department, or committee. This individual may delegate tasks. For assistance in identifying data owners or data authorities in ambiguous situations, see the ISO Domain 8: Asset Management Standard.
It is the duty of the Data Owner or Data Authority to:
- inventory and classify data according to the ISO Domain 8: Asset Management Policy;
- comply with the ISO Domain 9: Access Control Policy and the SSU Access Control Standard in authorizing, tracking, and documenting:
- end users of data,
- uses of data, and
- stewards of data (those who store and protect the data);
- work with the Information Security Office to identify an acceptable level of risk for the data;
- work with the Information Security Office to specify and document data controls and convey them to Data Users and Data Stewards. These controls must comply with the ISO Domain 8: Asset Management Standard, the SSU Physical Security standard, and SSU Access Control standard. These controls may include, but are not limited to, passwords, access control, encryption, physical locks, and backups;
- annually:
- confirm with Data Stewards that controls are in place, and
- review access lists;
- work with the Information Security Office to approve, justify, and document exceptions to security controls;
- perform other duties and fulfill other requirements described in the CSU Information Security Roles and Responsibilities Standard and any other CSU and SSU policies and standards when and as necessary.
7.2 Data Steward
Data Stewards are appointed and authorized by the Data Owner to store and protect the data. Examples include: Computer System Administrators, Database Administrators, and Managers of physical storage locations or facilities.
It is the duty of a Data Steward to:
- perform regular backups of the data;
- restore data from backup media;
- implement and follow all controls specified by the Data Owner and the Information Security Office;
- notify the Data Owner and the Information Security Office of any vulnerabilities impacting the security of the data, and of any actual or attempted violations of security policies, standards, practices, and procedures;
- perform other duties and fulfill other requirements described in the CSU Information Security Roles and Responsibilities Standard and any other CSU and SSU policies and standards when and as necessary.
7.3 Data User
Data Users are individuals who need and use University data as part of their assigned duties or in fulfillment of assigned roles or functions within the University community. Individuals who are given access to sensitive data have a position of special trust and as such are responsible for protecting the security and integrity of that data.
It is the duty of a Data User to:
- follow all CSU and SSU security policies and standards;
- use data only in authorized manners;
- follow all controls specified by the Data Owner and the Information Security Office;
- not subject any university information asset to a level of risk beyond that approved by the Data Owner;
- perform other duties and fulfill other requirements described in the CSU Information Security Roles and Responsibilities Standard and any other CSU and SSU policies and standards when and as necessary.
7.4 Information Security Officer
It is the duty of the Information Security Officer to:
- coordinate the campus information security program on behalf of the President;
- advise the President and his/her cabinet on all information security matters;
- work closely with campus administrators and executive officers on information security matters;
- oversee campus information security risk assessment activities;
- inform the President (or President designee) of significant information security risks as they are identified;
- oversee the campus information security incident response program in coordination with appropriate campus personnel;
- oversee the campus information security awareness and training program;
- provide input to the campus regarding information security risk mitigation activities and inputs regarding information security risks of proposed projects;
- respond to information security related requests during an audit;
- serve as the campus representative on the CSU Information Security Advisory Committee;
- avoid conflicts of interest by not having direct responsibility for information processing or technology operations for campus programs that employ protected information;
- provide input to campus Business Continuity and Disaster Recovery policies and procedures;
- perform other duties and fulfill other requirements described in the CSU Information Security Roles and Responsibilities Standard and any other CSU and SSU policies and standards when and as necessary.
8 Risk Management Standard
Implements ISO Domain 6: Organization of Information Security.
8.1 Risk Assessments
The Information Security Office will conduct on-going campus-wide information security risk assessments with the intent to assess each of the identified areas at least every two years.
8.2 Response to Identified Risk
Once a risk has been identified, the CIO, with assistance from the Information Security Office and the IT Project Management Office, will create a proposal to mitigate (including timeline and prioritization), transfer, or accept the identified risk. The Information Technology Advisory Group (ITAG) will review this proposal for approval on behalf of the university.
The response must reduce the risk to acceptable levels (risk mitigation), share or shift the risk to another party (risk transference), or assume the identified risk (risk acceptance). An information security risk can only be accepted by the President of the University and/or his/her designee.
8.3 Reporting
In compliance with the Incident Reporting Policy(ISO Domain 16: Incident Management Standard)
, the Information Security Officer will share appropriate information about campus wide information security risk with the CSU Chief Information Security Officer.
9 Personnel Security Standard
Implements Personnel Information Security Activities (ISO Domain 7: Human Resource Security Policy).
9.1 Revoking Access to Protected Data
When an employee no longer needs access to protected data due to a change of duties within a department, the employee’s Appropriate Administrator must notify the Data Owners of the protected data. The Data Owners must review the employee’s access and revoke any access not otherwise authorized.
When an employee no longer needs access to protected data due to an inter-department change of position, the employee’s former Appropriate Administrator, Human Resources, or Faculty Affairs, as appropriate, must notify the Data Owners of the protected data. Human Resources or Faculty Affairs, as appropriate, must send an email to the employee’s former Appropriate Administrator as a reminder of this requirement. The Data Owners must review the employee’s access and revoke any access not otherwise authorized.
When an employee ends their employment at Sonoma State University, the employee must clear campus as per the Sonoma State campus clearance process. Unless otherwise authorized, access to all campus protected data must be revoked. Human Resources or Faculty Affairs, as appropriate, must send an email to the employee’s former Appropriate Administrator as a reminder of this requirement.
9.2 Background Checks
Criminal Background Checks must be performed at the time of hire on any employee, staff, faculty, student assistant, consultant, volunteer, or other person performing work for the university, who will handle Level 1 Protected Data. These employees must be identified by their Appropriate Administrator when filling out the personnel requisition form.
9.3 Confidentiality Agreements
All employees, staff, faculty, student assistants, consultants, volunteers, and other persons performing work for the university must, at time of hire, sign a confidentiality agreement.
9.4 Disposition of Information Assets Upon Ending Employment
When an employee ends their employment at Sonoma State University, electronic and paper files must be promptly reviewed by an appropriate manager to determine who will become the data steward of such files and identify appropriate methods to be used for handling the files. If the separating employee is holding resources subject to a litigation hold and/or criminal investigation, the relevant information must be preserved until the litigation hold has been revoked, at which point the resource is subject to the normal record retention schedule.
Upon ending employment, if a former employee wishes it to obtain a copy of any personal electronic information stored on campus information assets, the former manager and Human Resources or Faculty Affairs, as appropriate, must either provide the personal electronic information to the former employee or allow the former employee to obtain the personal electronic information in a manner that preserves the integrity of all campus information assets.
10 Information Security Awareness Training Standard
Implements Information Security Training and Awareness Activities (ISO Domain 7: Human Resource Security Policy).
Because the following community members may come into contact with sensitive data in the course of their work, Information Security Awareness Training will be assigned annually to all SSU staff, faculty, administrators, currently working annuitants, consultants, auxiliary employees, student assistants, and volunteers with access to Sonoma State information technology resources.
The training must be completed within two months of its assignment, and will automatically be reassigned one year after completion.
11 Vulnerability Management Standard
Implements ISO Domain 12: Operations Security Policy.
11.1 Discovering Vulnerabilities
Vulnerabilities may be discovered in multiple ways, including but not limited to the following:
- Network-based vulnerability scans authorized by the Information Security Office;
- Penetration testing authorized by the Information Security Office;
- Security reviews performed by the Information Security Office;
- Vendor announcements;
- Published vulnerability information;
- Local discoveries.
11.2 Remediating Vulnerabilities
Remotely exploitable vulnerabilities that allow systems to be compromised and are being actively deployed against the University must be remediated as soon as a fix is available.
Other remotely exploitable vulnerabilities that allow systems to be compromised must be remediated no more than one week after a fix becomes available.
Other vulnerabilities must be remediated within 90 days.
11.3 Accepting Vulnerabilities
A reported vulnerability may be accepted only if:
- the reported vulnerability does not represent an actual vulnerability; or
- the risk associated with the vulnerability is mitigated by a compensating control.
12 Monitoring Standard
Implements Information Asset Monitoring (ISO Domain 12: Operations Security Policy).
Campus information systems and assets must implement logging and monitoring, including appropriate limitations on the collection, access, and use of all logs and monitoring data, and must protect, retain, and dispose of all logs and monitoring data, as described in the CSU Information Technology Security Policy, the Logging Elements (ISO Domain 12: Operations Security Standard), and CSU Executive Order 1031 - Systemwide Records/Information Retention and Disposition Schedules Implementation.
13 Configuration Management Standard
Implements Configuration Management (ISO Domain 12: Operations Security Policy).
13.1 Default Configuration
All workstations, including laptops, upon purchase or transfer between departments should be set up with a standard configuration by IT that meets or exceeds the minimum workstation configuration standards issued by the CSU system. Departments wishing to configure and administer their machines differently must provide the CIO or CIO’s designee with an authorization signed by an appropriate administrator. Additionally, this alternate configuration must still comply with all SSU and CSU security standards and policies including the SSU Vulnerability Management Standard and the SSU Configuration Management Standard.
13.2 Anti-virus and Anti-malware
All workstations of a type commonly affected by malicious software, including laptops, must have appropriate anti-virus and anti-malware software installed. The software and its malware definitions must be updated regularly. The software must be configured to run a full scan weekly and must have “on access” scanning enabled to prevent malware from running. This software should be centrally managed by Information Technology.
13.3 Mobile Device Management
Mobile devices (with the exception of laptop computers) must not contain Level 1 Protected Data. These devices must only access services that are accessible from the public Internet.
13.4 Laptops
Those wishing to use a laptop for any purpose involving access to, or storage of, Level 1 Protected Data must identify, and receive approval from, the Data Owner. Additionally, the device must have IT supported whole disk encryption. Laptops are also subject to all workstation configuration and patching requirements.
13.5 Remote Computing
Level 1 Protected Data must never be stored on or accessed using personally owned devices. All Level 1 Protected Data transported off campus for remote computing usage, or accessed from off campus, must only be stored on or accessed using campus issued computers and storage devices. These computers and devices must be configured with full disk encryption and must comply with the SSU Configuration Management Standard. As with all other storage, transportation, and use of Level 1 Protected Data, all remote storage, transportation, and use of Level 1 Protected Data must be approved by the appropriate Data Owner.
All devices, including personal devices, used to store or access Level 2 Protected Data must comply with the SSU Configuration Management Standard.
13.6 Operating System and Software Updates
13.6.1 Workstations
Workstations that are centrally managed by IT will automatically receive operating system and software updates at least quarterly. Those workstations that are not centrally managed should be running a currently supported operating system and should receive operating system and software updates at least quarterly.
13.6.2 Servers
Servers should be running a currently supported operating system and should have their operating system and software updated at least quarterly.
13.6.3 All other devices
All other devices connected to the Sonoma State network should be currently supported by the vendor. Operating system, software, and/or firmware updates should be applied within 90 days of release.
13.6.4 Exceptions
Operating system and software updates may be postponed if an update will cause issues such as incompatibility with other software. Exceptions must be documented and renewed at least annually.
14 Change Control Standard
Implements Change Control (ISO Domain 12: Operations Security Policy).
All configuration changes to information assets or systems that process, store, receive, transmit, or use CSU protected Level 1 data must be tracked and documented. The documentation must include:
● the nature of the change;
● the expected and potential impact of the changes, including security implications;
● whether or not the change can be undone if needed, and if so, how;
● the identity of the person making the change;
● the identity of the person reviewing and approving the change;
● the time that the change was made; and.
● the results of testing the change.
Changes should be scheduled so as to keep the impact upon users of any affected services to an acceptable level.
Departments responsible for information assets or systems that process, store, receive, transmit, or use CSU protected Level 1 data must:
- establish criteria, based on risk, that specify when stakeholders must be notified of intended changes and given an opportunity to offer input or raise concerns;
- establish criteria, based on risk, that specify when changes must be formally approved by an appropriate administrator; and
- formally identify individuals who are authorized to make emergency changes that, due to urgency or criticality, need to occur outside of the department’s formal change management process. Such emergency changes must be appropriately documented and promptly submitted, after the change, to the department’s normal change management process.
Appropriate stakeholders must be notified about completed changes and system documentation must be updated to reflect these changes.
15 Access Control Standard
Implements ISO Domain 9: Access Control Policy.
15.1 Authorization
Access to Protected Data must be denied until specifically authorized. Authorization to access Level 1 Protected Data must be granted on a per user basis by the Data Owner of the data to be used using the SSU Request for Access to Protected Data form. These authorizations must follow the principles of need to know, operational need, least privilege, and separation of duties. Data Owners must track any access modifications.
15.1.1 Third Parties
Third parties wishing to access Level 1 Protected data must also receive authorization from affected Data Owners, and must follow all applicable CSU and SSU policies, standards, laws, and contracts.
15.1.2 Review
Data Owners must review and renew all access authorizations on a specified date annually. This must be logged on the request form used for the original authorization. This review must include an evaluation of what level of access individuals need to perform their current job function. Access unrelated to legitimate business activities must be revoked.
15.2 Authentication
15.2.1 Unique Credentials
Unique credentials should be used for accessing all campus information systems.
Exceptions allowing the use of shared credentials must be approved by the requesting departments’ manager and by all affected data owners. The manager and all affected data owners must be informed of the associated risks. The department administering the system being accessed with shared credentials must track all shared credentials in use, must require shared credentials to be reauthorized at least annually, and must deactivate any shared credentials that are not reauthorized.
15.2.2 Keeping Personal Credentials Private
Personal Sonoma State credentials must remain private at all times. The credentials to an account can be used in malicious ways that could cause harm to an individual or the university.
Users should not under any circumstances share their personal password with anyone, whether affiliated with the university or not.
15.2.3 Issuing Credentials
When passwords are issued they must be one-time Passwords/Keys. One-time passwords (e.g., passwords assigned during account creation, password resets, or as a second factor for authentication) must be set to a unique value per user and changed immediately after first use.
15.2.4 Central Authentication
All production SSU web applications used by campus community members must perform centralized authentication based on Seawolf IDs and passwords.
Non-IT run services, including all outsourced services, must use an authentication technology (such as CAS or Shibboleth) that does not expose the password to the web application server.
15.2.5 SSL Login Requirement
When authenticating to any service hosted on Sonoma State’s network, or any service provided by a third party on behalf of Sonoma State, the communication of credentials must use secure settings and strong encryption mechanisms such as SSL or TLS. For example, webpages into which one types a password must use HTTPS instead of HTTP.
15.3 Passwords
15.3.1 Requirements
Password minimum length, complexity requirements, expiration, and lockout after failed logins must meet NIST level 1 “resistance to guessing authentication secret” as per the ISO Domain 12: Access Control Standard
To contain the damage resulting from a service compromise, and to minimize the potential harm to both SSU and individual users, SSU passwords must not be reused with non-SSU services such as personal email, social media, personal banking, and Internet message boards.
15.3.2 Storage
Passwords stored in any non-electronic form must be protected with appropriate controls, including but not limited to being locked up or carried on one’s person at all times.
Any passwords stored electronically (except for service accounts) must be stored using IT-supported encrypted password management software.
15.4 Public and Shared Resources
Level 1 or 2 Protected assets must never be made public. Campus personnel are encouraged to use discretion and good judgment when deciding what other information to make public, and must comply with all applicable SSU and CSU policies and standards, all applicable laws, and all applicable contractual requirements, when doing so.
16 Data Inventory Procedure
Implements ISO Domain 8: Asset Management Policy.
Annually, SSU will conduct an inventory of Level 1 data (as defined by the CSU Data Classification Standard). This inventory will be completed by distributing a Level 1 Data Inventory Survey to all identified data owners and Admin II managers or higher.
This survey is to be completed and returned to the Information Security Office.
The Information Security Office will be available to help users complete the Data Inventory survey by appointment.
17 Cloud Procurement Standard
Implements CSU Cloud Storage and Services (ISO Domain 8: Asset Management Standard)
The purpose of this standard is to ensure that CSU data is appropriately stored or shared using public cloud computing and/or file sharing services.
Per the CSU Standard, cloud computing and file sharing is defined as the utilization of an information technology service of any type that is not provided by servers which are owned/leased by the CSU or auxiliaries including, but not limited to, social networking applications, file storage, and content hosting.
Examples of cloud services include web-based email, web-based file storage, and other web-based services that are hosted by a vendor rather than being run locally on campus.
Only authorized third-party services or hosted services may be used to access, exchange, store, process or analyze campus data, or to provide the campus with critical operational technologies. Only Procurement is authorized to contract with third-party or hosted service providers.
Even if a service is free of charge, including trial periods, only Procurement is authorized to enter into a contract for its use. This includes any website requiring a "Click to Accept" action to access the services.
The department purchasing a cloud service must provide IT with:
- the Technology Purchase Review request; and
- a VPAT supplied by the vendor. (If you cannot find a VPAT, IT will search for one.)
The Technology Purchase Review form allows for a technical feasibility check in addition to supportability. The department must also provide a clear description of the application or service within the Technology Purchase Review form.
A VPAT must be filled out and submitted to IT for a review. The initial IT review typically takes no more than five business days. Once reviewed, IT will then return the forms either approved or denied. If approved, the department will need to fill out an EREQ for Purchasing. If denied, IT will work with the department and Purchasing on alternatives.
The department purchasing a cloud service must fill out and provide Purchasing with:
- Department Cloud Usage Checklist (Seawolf ID required); and
- the EREQ (E-Requisition, including the approved Technology Purchase Review Request and the VPAT)
The Department Cloud Usage Checklist elaborates on what kind of data is being stored and how said data will be accessed. EREQ or E-Requisition is required when purchasing any cloud service.
The vendor must provide Purchasing with at least one of the Security Practices Checklists referenced in 5.3 of the Cloud Storage and Services (ISO Domain 8: Asset Management Standard).
During Purchasing's review of the contract, if one or more of the following are true, then the ISO will evaluate the risk of the third-party service or hosted service.
- if the third-party/hosted service will be storing level 1 or 2 data,
- if the vendor wishes to deviate substantially from the IT Supplemental Provisions,
- if the service is unable to use Sonoma State's Central Authentication, or
- if there are any security concerns that are identified during the review.
At any point in the evaluation of a service, the ISO holds the right to evaluate the risk of the third-party service or hosted service.
18 Information Asset Management
Implements CSU Cloud Storage and Services (ISO Domain 8: Asset Management Standard)
The purpose of this standard is to ensure that SSU data is appropriately stored or transmitted.
18.1 Storage and Transmission of Sensitive Data
The following table provides information about appropriate methods for storing and transmitting different levels of data
| Application / Hardware | Level 1 | Level 2 | Level 3 | Any data encrypted using strong encryption (Level 1, 2 or 3) |
|---|---|---|---|---|
| Adobe Sign | Yes | Yes | Yes | Yes |
| Encrypted flash drive (Apricorn, Corsair) | Yes | Yes | Yes | Yes |
| Hard drives with full disk encryption | Yes | Yes | Yes | Yes |
| OnBase | Yes | Yes | Yes | Yes |
| Qualtrics | Yes | Yes | Yes | N/A |
| MoveIT Transfer | Yes | Yes | Yes | Yes |
| Yuja | Yes | Yes | Yes | N/A |
| Zoom | Yes | Yes | Yes | N/A |
| SSU-Alpha file server | Yes | Yes | Yes | Yes |
| SSU-Beta file server | No | Yes | Yes | Yes |
| SSU-Google Drive | No | Yes | Yes | Yes |
| SSU-Google Forms | No | Yes | Yes | No |
| Drupal Forms | No | Yes | Yes | No |
| Unencrypted flash drive | No | Yes | Yes | Yes |
| Unencrypted external hard drive | No | Yes | Yes | Yes |
| SSU-Email | No | Yes | Yes | Yes |
Some examples of strong encryption include:
- PDFs encrypted with compatibility set to "Acrobat 7.0 and later (PDF 1.6)" or "Acrobat X And later (PDF 1.7)";
- Zip files encrypted using AES-256 encryption and NOT standard zip encryption; (These can be created using 7zip and WinZip.)
- Password protected files created with Microsoft Office 2007 or newer; and
- Email encrypted with S/MIME.
Files must be encrypted using a strong password that is not stored or transmitted with the encrypted files, and not transmitted using the same medium. For example, it is acceptable to email an encrypted PDF and communicate the password over the phone.
Please contact the IT Help Desk at [email protected] or (707)664-HELP for assistance with securely storing sensitive information.
18.2 Data Sharing Guidance for Information Security Threats and Vulnerabilities
SSU community members who receive information about information security threats and vulnerabilities that are labeled with a Cybersecurity & Infrastructure Security Agency (CISA) Traffic Light Protocol (TLP) designation are required to follow the TLP sharing guidance for that designation.
18.3 Media disposal and reuse
When disposing of paper containing Level 1 or Level 2 data, it must be shredded with a crosscut shredder.
When disposing of electronic storage media, it must be securely erased or destroyed using IT approved procedures.
All electronic storage media must be securely erased using IT approved procedures before being redeployed to a new user .
19 Information Security Incident Response Standard
Implements ISO Domain 16: Incident Management Standard.
19.1 Information Security Incident Response Team Membership
The core Information Security Incident Response Team (ISIRT) consists of representatives from:
- Seawolf Services;
- Human Resources;
- Information Security Office;
- Information Technology Infrastructure;
- Information Technology Workstation Support;
- Networking;
- Marketing & Communications;
- Police;
- Risk Management.
19.2 Types of Incidents
The Information Security Incident Response Team (ISIRT) will investigate and respond to Information Security incidents involving malware, fraud, harassment, inappropriate use, unauthorized data access, unauthorized physical access, unauthorized system access, unauthorized system use, lost or stolen equipment, other violations of applicable Information Security laws, policies, standards, procedures and contracts, and other violations of the confidentiality, integrity, or availability of information systems or assets for which Sonoma State University holds responsibility.
19.3 Incident Response Procedure
19.3.1 Detection of Incidents
Some possible ways of detecting events include:
- Unusual network activity;
- Unusual server log entries;
- A denial of service (workstation, network, or service);
- The University is contacted by other organizations;
- The University is contacted by Police Services;
- The University is contacted by an end-user noticing strange behavior; or
- Alerts from security monitoring systems.
Detection can often occur at:
- A network perimeter (network firewall or network Intrusion Detection System);
- A host perimeter (host based firewall);
- On the system-level (on the host itself);
19.3.2 Reporting
Persons who suspect a security incident should contact the SSU IT Help Desk in one of the following ways:
- Send email to [email protected]; or
- Call 707-664-HELP (contact by email if there is no answer); or
- Visit the SSU IT Help Desk at the main entrance to IT, on the first floor south wing of the Schulz Information Center.
Please inform the IT Help Desk of the nature of data stored and accessed on any system suspected of being compromised, to the extent that this can be done without using or accessing the system itself.
Callers should state, in particular, if CSU protected level 1 or 2 data violations are suspected such as Social Security Numbers, medical information, grades, or other CSU protected level 1 or 2 data as defined in The Data Classification Levels (Asset Management ISO Domain 8 Standard).
19.3.3 Loss or Theft of Equipment or Media
When a computing device has been lost or stolen, an equipment loss report must be filed with Property Management.
When a computing device has been stolen, the theft must also be immediately reported to The Sonoma State Police Department.
When a computing device or a piece of storage media containing protected level 1 data has been lost or stolen, it must also be immediately reported to the Information Security Office. The Information Security Office will then follow the SSU Information Security Incident Response Procedure. Storage media includes, but is not limited to, storage devices, USB drives, paper, and any other storage media.
19.3.4 Notification of CSU Chief Information Security Officer
If a reasonable suspicion exists that Level 1 data has been breached, the Information Security Officer, in consultation with the Chief Information Officer (CIO), must notify the CSU Chief Information Security Officer and the SSU Emergency Management Office as soon as possible of the potential incident.
19.3.5 Preservation of Evidence
If a system is suspected of having been compromised, to avoid inadvertently destroying valuable evidence needed to protect other systems and to prove that protected information was not accessed, users and IT support staff must not:
- install or run any additional services, patches, upgrades, or other fixes;
- run anti-malware scans or backup software; or
- use the machine further for any purpose.
The Information Security Office has forensic software to preserve as much of the evidence as possible from a compromised computer.
19.3.6 Containment of Damage
If a compromised system is believed to be exfiltrating data or attacking other systems, the system must be immediately disconnected from the network.
If the presence of malicious software has been detected then the machine in question must immediately cease to be used and must be disconnected from the network. The Information Technology Help Desk must be notified. The machine must be examined for sensitive data and fully cleaned before use can continue.
19.3.7 Incident Investigation
The Information Security Office will, with assistance, as needed, from members of the Information Security Incident Response Team (ISIRT) and other campus community members, investigate and document the incident, and attempt to determine what information assets may have been involved, what damage may have been caused, what data may have been breached, and the identity and actions of the perpetrators. When a crime is known or suspected to have been committed, or when there is a possibility that notifications under the California Civil Code will be made, the Information Security Office will file a police report with the Sonoma State Police Department.
All campus community members must work with the Information Security Office, the Data Owner, the Data Steward, and/or other authorized individuals during the investigation and mitigation of information security incidents and breaches.
19.3.8 Recovery and Remediation
The Information Security Office will work with the affected parties to create and implement a plan to recover from the incident and remediate damage caused by the incident.
Where appropriate, violations of laws, policies, standards, procedures, contracts, or codes of conduct will be referred to other departments such as the Office of Student Conduct, Employee Relations and Compliance, Residential Life, or Faculty Affairs for further investigation or action.
19.3.9 Determining Notification Requirements
If confidential information is involved and if there is reasonable belief that it was compromised, the following actions are taken:
The Information Security Officer and/or the CIO will make a recommendation to the President about whether to make a formal breach notification. The Information Security Officer and/or the CIO will be advised by Senior Management as available and appropriate, including:
- Vice President of Administration and Finance;
- Vice President of University Affairs;
- Strategic Communications representative;
- Web Services Director; and
- Director of Risk Management.
The President or designee will decide whether the University is to make a formal breach notification; If a breach notification is to be made:
- The President or designee will decide whether to notify individually, through the media, or both, and assigns tasks;
- A draft copy of the notification must be sent to the CSU Chief Information Security Officer for review;
- The notification will be sent to the user and/or published, as decided by the President.
Additional notifications are made according to ISO Domain 16: Incident Management Standard and other contractual and legal requirements. These include but are not limited to:
- If a breach of level 1 data has occurred, the President notifies the Chancellor, the CIO notifies the Assistant Vice Chancellor for Information Technology Services, and the campus ISO notifies the CSU Chief Information Security Officer using the Chancellor’s Office Security Incident Response Form;
- If a breach of PCI data has occurred, the affected payment brands are notified and the appropriate procedures are followed from the payment brand incident response procedures; and
- Breaches involving data exchanged with other entities are reported to those other entities as appropriate.
Follow up meetings are held to monitor the status of the notification effort.
19.3.10 Handling Inquiries
In the event that notification of the incident is given to members of the public or the campus community, the Information Security Incident Response Team (ISIRT) will work with Strategic Communications to determine what methods will be used for handling inquiries about the incident. Possible methods include but are not limited to the creation of a website dedicated to the incident and the temporary use of the campus information/emergency phone line message.
19.3.11 Follow-up
The Information Security Office will lead a follow-up conversation to identify and apply lessons learned, and to develop and implement corrective actions directed at preventing or mitigating the risk of similar occurrences.
19.3.12 Closing the Incident
When all outstanding action items have been completed, the Information Security Office will close the incident and notify the President and the Information Security Incident Response Team (ISIRT).
20 Physical Security Standard
Implements ISO Domain 11: Physical and Environmental Security Policy.
20.1 Purpose
All areas containing Level 1 Protected data must be physically protected as per the ISO Domain 11: Physical and Environmental Security Policy.
20.2 Identifying Security Zones
Shared Access Areas and Campus Limited Access Areas will be identified based on responses to the annual Data Inventory Survey and criteria set by the ISO Domain 11: Physical and Environmental Security Standard.
20.3 Appropriate Controls
20.3.1 Viewing Controls
The display screens for all campus information systems that have access to protected data must be positioned such that data cannot be readily viewed by unauthorized persons (e.g., through a window, by persons walking in a hallway, or by persons waiting in reception or public areas). If it is not possible to move a display screen to meet the above requirement, a screen filter must be used.
20.3.2 Shared Access Areas
- Doors controlling access to the area should be locked when the area is unattended;
- Entrance to the area should be monitored and controlled by a trusted individual when the doors are unlocked;
- Guests should always be monitored by persons who can prevent unauthorized access to the protected information assets or critical systems in the area;
- Assets that contain or access Level 1 Protected data and can be removed by a single individual, including but not limited to computers or small lock boxes, must be physically locked down, must be directly supervised at all times, or must utilize full disk encryption. These include, but are not limited to, computers, storage devices, storage media, USB drives, paper, and small lock boxes;
- Cabinets containing Level 1 Protected data must be kept locked, may only be unlocked while the contents are being accessed, and must be relocked immediately afterwards;
- Workstations that store, process, transmit, or access Level 1 Protected data must be locked with a password when unattended. This password must comply with the password requirements in the SSU Access Control standard.
20.3.3 Campus Limited Access Areas
- Doors controlling access to the area must always be locked;
- Guests must always be logged and monitored by persons who can prevent unauthorized access to the protected information assets or critical systems in the area;
- Cabinets containing Level 1 Protected data must be locked when unattended;
- Workstations that store, process, transmit, or access Level 1 Protected data must be locked with a password when unattended. This password must comply with the password requirements in the SSU Access Control standard;
- Authorization to access the area must be explicitly granted and documented;
- Where supported by access controls (for example, card locks), access to the area must log access times and the identity of individuals accessing the area.
21 Compliance Standard
Implements ISO Domain 18: Compliance Policy.
21.1 PCI DSS (Payment Card Industry Data Security Standard)
In accordance with CSU Debit/Credit Card Payment Policy, all people, processes, and systems within the scope of the Payment Card Industry Data Security Standard (PCI DSS) must comply with the PCI DSS in the manner(s) specified by the SSU PCI Data Authority.
21.2 Legal Compliance
All University business must be conducted in compliance with all applicable laws, including but not limited to FERPA (Family Educational Rights and Privacy Act), GLBA (Gramm-Leach-Bliley Act), and HIPAA (Health Insurance Portability and Accountability Act).
21.3 Identity Theft Prevention and Red Flags (FTC Red Flags Rule)
21.3.1 Definition and Purpose
A red flag is an event or observation that indicates a heightened probability of identity theft.
Identity theft is strongly related to credit fraud, and Sonoma State University extends credit to students in the form of Student Loans and Payment Plans.
This standard describes examples of red flags to notice, should they appear in the course of daily business, and direction in responding to red flags.
21.3.2 Possible Red Flags
Red flag events include notification of the University by law enforcement, a credit reporting agency, a victim of identity theft, or another party, that an identity theft has occurred or is suspected of having occurred.
Red flag observations can include anything suspicious about a customer, documents provided, or information provided.
Customer red flags include inconsistencies between the customer's appearance or voice and the photograph or physical description in University records or on the presented identification.
Document red flags include any evidence that a piece of identification, a form, or any other document, has been forged, altered, or destroyed and reassembled.
Information red flags include:
- Information, including signatures, conflicting with other information provided by the customer, on file with the University, or available from external sources;
- Information expected to be unique to an individual, such as a Social Security number, being shared by multiple customers;
- Social Security Numbers that have not been issued or that appear in the Social Security Administration’s Death Master File;
- Contact information known by the University to have been previously used for fraudulent purposes.
21.3.3 Detection of Red Flags
Some red flags are detected automatically, such as certain kinds of invalid information, some red flags are detected through manual observation, and some are only detected when suspicious circumstances have prompted investigation. Most red flags are most likely to be discovered during the process of authenticating a student.
21.3.4 Response to Red Flags
The detection of a Red Flag by an employee shall be reported to their appropriate administrator and to the IT Helpdesk as per the Sonoma State Information Security Incident Response Standard.
Based on the circumstances and the type of red flag, the Appropriate Administrator and the Information Security Incident Response Team, together with the employee will determine the appropriate response.
Appropriate responses may include:
- Enhanced authentication measures;
- Contacting the individual;
- Not lending money;
- Not attempting to collect on a debt or not selling a debt to a debt collector;
- Notifying law enforcement; or
- Determining that no response is warranted under the particular circumstances.
21.3.5 Service Providers
The University remains responsible for compliance with the Red Flags Rule even if it outsources operations to a third party service provider. The written agreement between the University and the third party service provider shall require the third party to have reasonable policies and procedures designed to detect relevant Red Flags that may arise in the performance of the service provider’s activities. The written agreement must also indicate whether the service provider is responsible for notifying only the University of the detection of a Red Flag or if the service provider is responsible for implementing appropriate steps to prevent or mitigate identify theft.
21.3.6 Training
All employees who process any information related to a covered account shall receive training to understand their responsibilities associated with the Identity Theft Protection Standard.
22 Enforcement and Investigation Standard
Implements CSU Enforcement Policy.
Investigations involving employees and students suspected of violating the CSU or SSU Information Security policy must be conducted in compliance with all applicable laws, regulations, collective bargaining agreements, and CSU and SSU policies.
SSU reserves the right to temporarily or permanently suspend, block, or restrict access to information assets, independent of such procedures, when it reasonably appears necessary to do so in order to protect the confidentiality, integrity, availability, or functionality of SSU resources or to protect SSU from liability.
23 Credits and Acknowledgements
Written and maintained in consultation with:
- Accounting
- Compliance
- Computer Science
- Faculty Affairs
- Financial Aid
- Human Resources
- Information Technology
- Institutional Research
- Procurement
- Risk Management
- School of Education
- Seawolf Services
- Strategic Communications
- Student Affairs
- University Advancement
- University Police
Portions derived, with permission, from the San Diego State University Information Security Plan.
Portions derived, with permission, from the Sacramento State Information Security Policies and Standards.
Portions derived, with permission, from the Cal Poly Policies, Standards, Guidelines, Procedures, and Forms.
Transcript
- Login to your macOS workstation with your campus credentials
- From the "Go" dropdown menu, select Applications
- Scroll down to and Open the "Self Service" Application
- Select the "macOS FileVault Encryption" icon, or the "Encrypt" button
- Select "Encrypt" button
- The install process will run automatically for about 30 seconds
- Your workstation will restart and return you to the updated login screen
- Login to your macOS workstation with your campus credentials
- Select "OK" to allow fdesetup to enable FileVault
Malware, short for malicious software, consists of programming (code, scripts, active content, and other software) designed to disrupt or deny operation, gather information that leads to loss of privacy or exploitation, gain unauthorized access to system resources, and other abusive behavior. (excerpted from Wikipedia: Malware)
What can I do about Malware?
For Students
In order to keep students up to date with their class assignments and to keep SSU a safe computing environment, it is highly recommended that students have antivirus software on their personal computer when connecting to our network. It is recommended that for your computer is scanned once a week and that your software is configured to look for new virus definitions from the software company that made it. While the specific choice of software is ultimately up to the student, below is a sample list of popular free and paid antivirus options.
Note: Any existing antivirus software must be removed from your computer before installing a new antivirus software. Failure to do so may cause problems with system performance, internet connectivity, and lower the effectiveness of the antivirus protection.
Free Antivirus Options
Windows Defender (Windows 8 & 10)
Windows Defender is a Microsoft antivirus solution that comes pre-installed on every computer with Windows 8 or later. Because Windows Defender is made by Microsoft to integrate seamlessly into the Windows Operating System, it tends to be an effective, fast, and nonintrusive option. The SSU IT Help Desk highly recommends this choice. It is not possible to remove Windows Defender, so if you decide to use a third party antivirus solution instead, the new software will automatically disable the built in antivirus.
Microsoft Security Essentials (Windows 7)
Microsoft Security Essentials is a Microsoft antivirus solution that can be downloaded for free directly from Microsoft. Like Windows Defender, this software is designed to integrate seamlessly into the Windows Operating System and is therefore highly recommended for those running Windows 7.
Paid Antivirus Options
If you are protected and happen to still get infected, please bring your computer to the IT Help Desk in Schulz 1000 and we can help you get the malware removed.
For Staff and Faculty
If you have a state tagged computer and believe that you may be infected please turn off your computer and contact the Help Desk at 664-4357.
Physical Security for Mobile Devices
Scammers and criminals aren't only a threat online. They can use your device to access information, and may sabotage or even steal the device itself. Keep an eye on your computers, phones, tablets, and other devices.
- Don't leave any mobile devices unattended, especially in a shared space.
- Password protect mobile devices.
- Lock your screen when you step away from your desktop.
- Avoid accessing banking or other sensitive information on shared devices.
- Don't install software on campus computers without authorization.
- If you find a USB drive, leave it with lost and found. Do not plug it into your computer!
- Be aware of suspicious behavior, such as unauthorized attempts to access non-public areas, or unauthorized attempts to use, remove, or alter equipment.
- Immediately report suspicious behavior to Police & Safety Services at (707) 664-4444.
- Verify the identity of any third-party persons claiming to be repair or maintenance personnel, prior to granting them access to modify or troubleshoot devices. Do not install, replace, or return devices without verification. Some forms of verification may include contact with the vendor or contractor, contact with IT, or information from a coworker who coordinated the maintenance.
Network and Wireless Security
Why is wireless Internet security important?
Good wireless security practices can reduce the risks of having your computer, online accounts, or personal information compromised.
When is it generally safe to enter logins, passwords, payments, or other personal information into a website?
When all of the following are true:
- You are accessing the website using an address (URL) that begins with HTTPS:
- Your browser has not issued a warning about the website certificate.
- The website belongs to an organization with whom you are comfortable sharing the information.
Which network should you connect to?
SSU-SECURE is the recommended, encrypted wireless network at SSU.
What precautions should I take when working from an open Wi-Fi network, such as at a restaurant or coffee shop?
- Avoid highly sensitive activities such as accessing level 1 data at SSU, or
- connect to the SSU network using the campus VPN (Virtual Private Network). (Contact the IT Help Desk for assistance in configuring and using the campus VPN.)
Software Security
Malicious software, or "malware," can observe your behavior, steal information or passwords, cause additional advertisements to appear when browsing the web, or even use your computer, without your knowledge, to perpetrate further criminal activity.
To protect yourself from malicious software:
- Regularly apply software updates on all computing devices to operating systems and key software, including Mac, Windows, tablets, phones, and web browsers.
- Outdated software may have security holes that criminals can use to access your files and information.
- Due to known vulnerabilities, avoid using Java and Flash whenever possible.
- Use anti-virus software. (Sonoma State offers this at no charge.)
- Report any symptoms of malware to the IT Help Desk (slowness, pop-ups, new and unexpected icons/toolbars, etc.).
- Faculty and staff only: Contact the IT Help Desk for help with software installs and updates on university devices.
Level 1 Data
What is Level 1 data?
CSU protected Level 1 data could be used to cause a high level of harm to the University or an individual. We have a high level of responsibility to protect this data.
Level 1 data must never be stored or accessed using personally owned devices, including mobile devices, and may only be stored or accessed using devices owned by Sonoma State University and managed by the SSU IT department.
CSU protected Level 1 data includes but is not limited to:
- Social Security number with name.
- Birth date combined with last four digits of SSN and name.
- Credit card numbers.
- License number or other government issued identification number.
- Health information, including records and insurance.
- Bank account or debit card information with any required security credentials.
For a complete definition of Level 1 data, view the CSU Data Classification Standard.
Handling Level 1 data
Do NOT:
- Gather or keep Level 1 data without a pressing business need.
- Disclose Level 1 data to unauthorized recipients in any manner, including but not limited to, verbally, in written form, or in electronic form.
- Save unencrypted level 1 data to your local drive, such as the desktop or the Downloads/Documents folders.
- Store level 1 data on personal computing devices.
- Send or forward level 1 data via email.
Do:
- Ask yourself if you really need to store the information. If you must, follow the appropriate CSU and SSU standards.
- Use discretion in deciding when and how publicly to discuss sensitive information.
- Dispose of Level 1 data properly by cross shredding paper copies or returning them to their owners, and having IT securely erase electronic media.
- Ensure that all paper and electronic media containing Level 1 data is secured or directly supervised at all times.
Level 2 Data
What is Level 2 data?
CSU protected Level 2 data is data which must be protected due to proprietary, ethical, contractual or privacy considerations, or which may not be specifically protected by statute, regulations, or other legal obligations or mandates but for which unauthorized use, access, disclosure, acquisition, modification, loss, or deletion of could cause financial loss, damage to the CSU's reputation, violate an individual's privacy rights, or make legal action necessary.
All devices, including personal devices, used to store or access Level 2 Protected Data must comply with the SSU Configuration Management Standard.
CSU protected Level 2 data includes but is not limited to:
- Birth date (full: mm-dd-yy or partial: mm-dd only)
- Photo (taken for identification purposes)
- Grades/Courses taken/Schedule/Test Scores/Advising records/Educational services received
- Employee net salary
- Home address
- Personal telephone numbers
- Personal email address
- Payment History
- Employee evaluations
- Pre-employment background investigations
- Mother's maiden name
- Race and ethnicity
- Parents' and other family members' names
- Birthplace (City, State, Country)
- Gender
- Marital Status
- Physical description
For a complete definition of Level 2 data, view the CSU Data Classification Standard.
Handling Level 2 data
Do NOT:
- Gather or keep Level 2 data without a pressing business need.
- Disclose Level 2 data to unauthorized recipients in any manner, including but not limited to, verbally, in written form, or in electronic form.
Do:
- Ask yourself if you really need to store the information. If you must, follow the appropriate CSU and SSU standards.
- Use discretion in deciding when and how publicly to discuss sensitive information.
- Dispose of Level 2 data properly by cross shredding paper copies or returning them to their owners, and having IT securely erase electronic media.
- Ensure that all paper and electronic media containing Level 2 data is secured or directly supervised at all times.
What is multi-factor authentication, or two-factor authentication?
MFA is a login method that confirms a user's identity by prompting for two or more factors prior to a successful login. Users verify that they both know their password (unique knowledge), and that they also possess a hardware token or device running the Duo app (unique possession).

Learn more about Duo multi-factor authentication with this video.
Why are we implementing MFA?
MFA is a standard security practice across higher education that is highly effective at ensuring organizations stay safe and secure. Verifying your identity using a second factor prevents anyone but you from logging in, even if that other person knows your password. All students, faculty, and staff are required to use MFA when accessing their Seawolf account.
How do I get set up?
Contact the SSU IT Help Desk. Set up takes approximately 10 minutes. Have your smartphone or tablet with you if you wish to use the Duo App.
How does MFA work?
When you log in to the Sonoma State homepage, you will be taken to a second screen that will require you to either select "Send Me A Push," which will send a notification to your enrolled device for authorization within the Duo application, or enter a 6-digit number from your physical token or Duo app. If you select the "Remember me for 12 hours" checkbox, you will not be prompted for MFA for 12 hours on that device and browser.
How do I update my MFA devices?
Simply log in to the MFA Self Service tool to add and remove your MFA devices. You will need MFA to log in to the tool, so be sure to keep at least one MFA device active until you can add a new one.
What if I get an unexpected push notification?
Do not approve the request. This is an indicator that someone has your password and is attempting to log into your account. They cannot gain access without either approval from the Duo app or the 6 digits generated by your app or physical token. After you deny the request, flag the request as fraudulent, and change your Seawolf account password.
How do I get help with MFA?
Contact the IT Help Desk for all MFA-related questions.
Enroll In or Manage MFA:
Students use the MFA Self Service tool to enable MFA on their account or add and remove devices.
What is Multi-Factor Authentication, or MFA?
MFA is a login method that confirms a user's identity by prompting for two or more factors prior to a successful login. Users verify that they both know their password (unique knowledge), and that they also possess a hardware token or device running the Duo app (unique possession).
Learn more about Duo multi-factor authentication with this video.
Why are we Implementing MFA?
MFA is a standard security practice across higher education that is highly effective at ensuring organizations stay safe and secure. Verifying your identity using a second factor prevents anyone but you from logging in, even if that other person knows your password. All students, faculty, and staff are required to use MFA when accessing their Seawolf account.
How do I get Set up?
Students use the online MFA Self Service tool to enroll in MFA.
Once verified, you will be emailed a QR code to your Seawolf email that will allow you to auto-enroll your smartphone or tablet. All you'll need is the Duo Mobile app for iPhone or Android. This method allows you to authenticate via push notification or by entering a code generated within the app. It's quick, easy, and the Duo app is compatible with most devices.
If you experience any issues or need additional accommodations, contact the IT Help Desk for assistance.
How it Works
When you log in to the Sonoma State homepage, you will be taken to a second screen that will require you to either select "Send Me a Push," which will send a notification to your enrolled device for authorization, or "Enter a Passcode" where you will then enter in a 6-digit number from within the Duo app.
If you select the "Remember me for 12 hours" checkbox, you will not be prompted for MFA for 12 hours on that device and browser.
What if I Need to Add or Remove a Device?
You can manage your MFA devices from the MFA Self Service tool. You can have up to three devices associated with your account, so be sure to remove your old devices when you no longer need them.
What if I get an Unexpected Push Notification?
Do not approve the request. This is an indicator that someone has your password and is attempting to log into your account. They cannot gain access without being approved via the app, but you must secure your account. Deny the request, change your password, and contact the IT Help Desk.
Criminals are regularly sending phishing emails to some campus community members.
Phishers are criminals who attempt to impersonate an organization with whom you have an electronic account, such as your bank or Sonoma State University. They often attempt to deceive you into giving them your username and password, Social Security number, birth date or other sensitive information.
When should I suspect phishing?
- When you did not expect the email, or the email claims to be part of a transaction that you did no initiate;
- When the email contains obvious deviations from standard practice, such as when the To or From addresses are incorrect or missing, or when the message contains poor spelling and grammar, generic greetings or incorrect information;
- When the email contains threats, requests for money or sensitive information, or offers that seem too good to be true;
When, upon hovering over a link the target URL either does not match the displayed text, or is formatted deceptively; (For example,
http://www.sonoma.edu.example.com/and
http://www.sonoma.edu.edu@example.comare links to example.com and not to sonoma.edu) or
- Any other time when something just does not look right to you.
Cofense offers a handout at PhishMe: How to spot a Phish with additional tips on how to phishing attempts.
What should I do when I suspect an email may be phishing?
- If you are unsure whether an email is legitimate, verify the contents of the message with the corresponding institution. Do this online by typing the URL yourself, or offline by calling them with a phone number known to you, not with any information from the email itself.
- Report spam and phishing emails to Google and reduce the number of malicious emails you will receive in the future: Mark or unmark Spam in Gmail
- Never respond to a spam or phishing email. Responding just confirms that your email address is valid and you will find yourself getting more spam than ever.
- Never click on any links that look suspicious. The safest way to access your bank's website is to open a new web browser and type in the URL yourself (for example, www.example.com).
- Never open attachments in emails that look suspicious. This is a very common way for computers to get infected with malicious software, or "malware," that can observe your behavior, steal information or passwords, cause additional advertisements to appear when browsing the web, or even use your computer, without your knowledge, to perpetrate further criminal activity.
- Never provide account credentials and passwords through email.
- SSU IT will never ask you for your username and password in an email.
How can I securely store and access level 1 data from off-campus?
Per the SSU Information Security Information Asset Management standard, files containing unencrypted level 1 data must be stored on the SSU-Alpha encrypted file server, and must not be stored on a cloud storage service (such as Google Drive), on your network home drive (M: drive), on the SSU-Beta file server, or on an unencrypted flash drive or other external drive. They also must not be sent through email.
How do I access SSU-Alpha from off-campus?
In order to access SSU-Alpha from off-campus, you will need to:
- have a university issued Windows laptop,
- have full disk encryption enabled on your laptop,
- have multifactor authentication enabled for your account,
- have VPN (Virtual Private Network) access enabled for your account,
- have the VPN client installed on your laptop, and
- keep the Operating System on your laptop patched on an ongoing basis.
Please contact the IT Help Desk to set up your computer and your account to enable remote access to the SSU-Alpha fileserver.
CSU Information Security Standards require that the campus perform website vulnerability scanning for SSU websites.
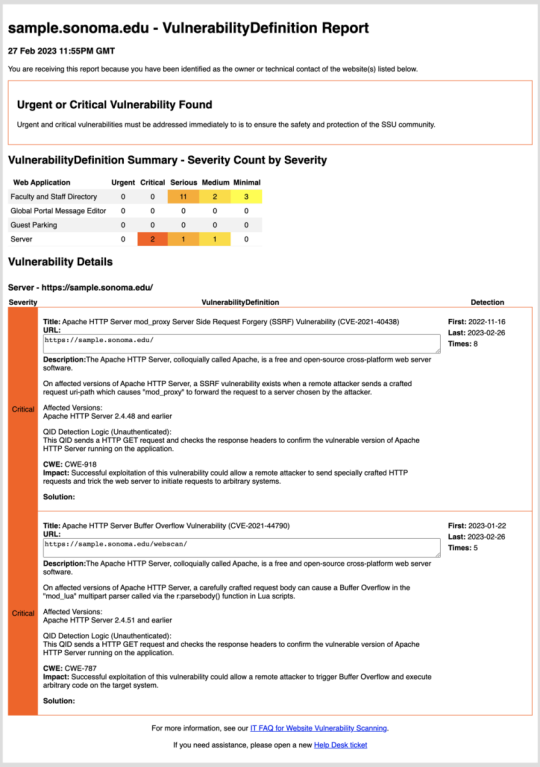
Screenshot of website vulnerability report.
Click to zoom.
Information Technology uses Qualys to run website vulnerability scans on a weekly basis. Reports are sent to website owners identifying urgent and critical issues that should be addressed by the website owners.
The types of sites and applications that will be scanned include public-facing sites that are any of these:
- Locally developed
- Locally hosted
- Locally administered and hosted with an Infrastructure or Platform as a Service provider
- Other sites as determined by Information Technology.
Website owners must immediately remediate the vulnerabilities by working with the site’s system and website administrators. Those may be SSU employees, vendors, or contractors.
If you have questions about your Website Vulnerability Report, please submit a Help Desk ticket. For quickest response, use the following format.
- Subject: Website Vulnerability Question
- Issue Type: Web Issue
- Description: Include the name and URL of your site, plus your question(s).
A Simple Electronic Signature (such as a check box on an authenticated web page or an email approving a request) may be used in lower risk situations where the university will not be heavily impacted should a signature be forged or should the university be unable to prove the validity of said signature.
A Digital Signature is a very specific form of an Electronic Signature which uses cryptography to establish the authenticity and validity of the signature with much greater certainty. For transactions where there is a greater risk to the University, or where a “wet” signature is typically required, Digital Signatures must be used instead of a Simple Electronic Signature.
For a Digital Signature to be valid, it must be created by a technology accepted for use by the State of California and conform to technologies capable of creating Digital Signatures as set forth in California Government Code Section 16.5:
- It is unique to the person using it;
- It is capable of verification;
- It is under the sole control of the person using it;
- It is linked to data in such a manner that if the data are changed, the Digital Signature is invalidated;
- It conforms to Title 2, Division 7, Chapter 10, of the California Code of Regulations.
The requirements for implementing Electronic and Digital Signatures are defined in the CSU Acceptable Use of Electronic and Digital Signatures (ISO Domain 10: Cryptography Standard.
Users are expected to use good judgment and reasonable care in order to protect and preserve the integrity of CSU equipment, its data and software, and its access. More details can be found in the CSU Responsible Use Policy.
CSU Data Classification Levels (Asset Management ISO Domain 8 Standard) explains the difference between Level 1, 2, and 3 Data.
Level 1 examples – Confidential information include but are not limited to:
- Passwords or credentials that grant access to level 1 and level 2 data
- PINs (Personal Identification Numbers)
- Birth date combined with last four digits of SSN and name
- Credit card numbers with cardholder name
- Tax ID with name
- Driver’s license number, state identification card, and other forms of national/ international identification (such as passports, visas, etc.) in combination with name
- Social Security number and name
- Health insurance information
Level 2 examples – Internal Use information include but are not limited to:
- Identity Validation Keys (name with)
- Birth date (full: mm-dd-yy)
- Birth date (partial: mm-dd only)
- Photo (taken for identification purposes)
- Student Information-Educational Records not defined as “directory” information, typically:
- Grades
- Courses taken
- Schedule
- Test Scores
- Advising records
- Educational services received
- Disciplinary actions
- Student photo
- Library circulation information
Level 3 - Information which may be designated by your campus as publically available and/or intended to be provided to the public:
- Information at this level requires no specific protective measures but may be subject to appropriate review or disclosure procedures at the discretion of the campus in order to mitigate potential risks
- Disclosure of this information does not expose the CSU to financial loss or jeopardize the security of the CSU’s information assets
Sections 4 and 5 of the CSU ISO Domain 8: Asset Management Standard explain the requirements for storing and handling Level 1 Data and Level 2 Data.
Each information asset containing Level 1 Data must have an identified Data Owner or Data Authority.
The Data Owner must classify the data and approve all users and uses of the data, storage locations for the data, and controls protecting the data.
Additional information about the Data Owner's responsibilities are defined in Section 7.1 of the SSU Information Security Management Program.
All uses of cloud services are subject to the CSU Cloud Storage and Services (ISO Domain 8: Asset Management Standard).
In order to use a third party service that stores or processes Level 1 Data or Level 2 Data:
- You must receive approval from the Data Owner or Data Authority, whose role is defined in Section 7.1 of the SSU Information Security Management Program, in order to store or process the data using the third party service.
- There needs to be a contract in place through purchasing (even if the service is free) that includes the appropriate IT Supplemental Provisions.
- The service, and your use of the service, must comply with the CSU ISO Domain 15: Supplier Relationships Standard.
- If this third party service is a cloud service then it must comply with the CSU Cloud Storage and Services (ISO Domain 8: Asset Management Standard).
- The process described in the SSU Cloud Procurement Standard must be followed for the purchase of the service.
What is the Cloud Procurement Standard and how does it apply to me?
In order to comply with CSU IT Security Policies, Sonoma State has implemented an Information Security standard to manage the risks of storing University data in the cloud.
Our goal is simply to mitigate risk and to protect student data. We are not focusing on a free phone “APP” is being used for instructional purposes, which does not contain confidential student data (level 1 or 2 data).
Cloud computing and storage is defined as the utilization of IT services provided by a 3rd party and NOT provided by servers in the local datacenter. Examples of cloud services include web-based email, web-based file storage, and other web-based services that are hosted by a vendor rather than being run locally on campus.
To protect the campus from liability, only Purchasing is authorized to enter into contracts with vendors. This includes "Click to Accept" contracts for free or trial services.
Please try to start the procurement process early because we must verify sufficient security and evaluate a vendor's practices and contract language, which can be time consuming. We recommend beginning the process 6 months before you need to use the service, if possible.
When the renewal comes due for a cloud service that was previously procured, the requester is asked to complete the Purchasing document called Department Usage Checklist. IT and Purchasing will perform the necessary compliance checks. Once reviewed, IT will then return the forms either approved or denied. If approved, the department will need to fill out an EREQ for Purchasing. If denied, IT will work with the department and Purchasing on alternatives.
Department trainings are available. Please contact Evan Ferguson at [email protected] or Jenifer Barnett at [email protected].
Why is wireless Internet security important?
Good wireless security practices can reduce the risks of having your computer, online accounts, or personal information compromised.
When is it generally safe to enter logins, passwords, payments, or other personal information into a website?
When all of the following are true:
- You are accessing the website using an address (URL) that begins with HTTPS:
- Your browser has not issued a warning about the website certificate.
- The website belongs to an organization with whom you are comfortable sharing the information.
Which network should you connect to?
SSU-SECURE is the recommended, encrypted wireless network at SSU.
What precautions should I take when working from an open Wi-Fi network, such as at a restaurant or coffee shop?
- Avoid highly sensitive activities such as accessing level 1 data at SSU, or
- connect to the SSU network using the campus VPN (Virtual Private Network). (Contact the IT Help Desk for assistance in configuring and using the campus VPN.)
What is Eduroam and how do I use it?
Eduroam provides on-campus Wi-Fi access to visiting faculty, staff and students from participating institutions utilizing their home institution credentials. It also provides SSU faculty, staff and students who will be visiting a participating institution the ability to connect to Eduroam while away. More information can be found at the Eduroam FAQ.
Can guests use Wi-Fi?
Guests of the university may receive a guest wireless account by being sponsored by an SSU student or employee. For details, see Guest Access to Wi-Fi.


